Modern detection for modern threats
At Chronicle, we believe it’s time for a better way to do detection. As the IT landscape becomes more complex and attackers continue to evade current security tools, it’s clear that attempts at prevention fall short. The rapid adoption of the ATT&CK framework also highlights the expanding threat attack surface and advancement of modern threats.

Today, we’re excited to announce the availability of Chronicle’s threat detection capabilities. Since joining Google Cloud over a year ago, the Chronicle team has been innovating on our investigation and hunting platform to bring you Chronicle Detect, a set of modern detection capabilities built on Google infrastructure to help you identify threats at unparalleled speed and scale.
Chronicle’s detection solution includes the next generation of our rules engine, a powerful rules language optimized to efficiently describe complex threat behavior, and an applied threat intelligence service that surfaces highly actionable threats in Chronicle environments based on Google’s collective insight and research into Internet-based threats.
For accurate threat detection, some important components are needed — the first is diverse, high value security telemetry to run detections on. High volume, rich data such as EDR or XDR data is tough to use effectively for investigation or detection due to limitations around scale, performance, and cost. Using our Google-scale platform, security teams can send their security telemetry to Chronicle at a fixed cost so that the full picture of security data can be taken into account for detections.
Data sent to Chronicle is incorporated into its Unified Data Model (UDM), a data model built for security telemetry relevant to threat detection such as EDR, NDR, DNS, proxy, and SaaS. Data in Chronicle’s UDM is enriched with context (e.g., asset, user, threat intelligence, and vulnerabilities) and correlation (e.g., IP to host), creating a platform that is broader than SIEM and builds toward the vision of XDR.
With Chronicle Detect, you can use advanced rules out-of-the-box, build your own, or migrate rules over from legacy tools. Our next generation rules engine enables analysts to easily build detection rules to detect complex threat behavior by operating on abstracted and enriched UDM data. It includes constructs for modern threat detection such as multi-event sequencing, aggregation, and windowing over planet-scale data volumes at Google speed. This means you can detect multi-event attack sequences such as a new email sender followed by an HTTP post to a rare domain; a suspiciously long powershell script accessing a low prevalence domain; or a low prevalence process accessing a low prevalence domain.
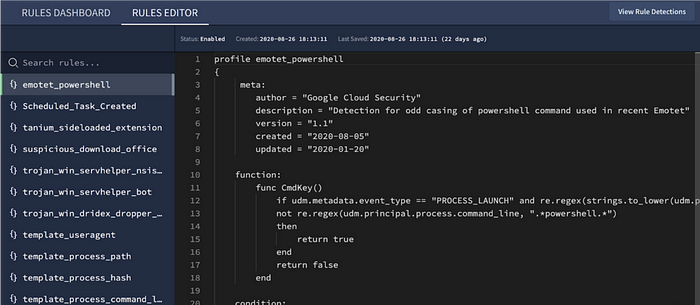
The capabilities of the Chronicle Detect rules engine are accessed using the YARA-L threat detection language which was designed by and for security practitioners to express complex threat behavior, not merely to query the data in order to eventually use it for detection. YARA-L is optimized to easily encapsulate complex threat behavior with concise syntax. The efficiency of the syntax is enabled by operating on a pre-enriched data model (UDM). As a result, detections that require complex and verbose syntax with joins, subqueries and lookups in other platforms can be expressed with a few lines of readily comprehensible syntax using YARA-L. This makes rule authoring, as well as alert triage, accessible to a larger segment of any organization’s security analyst community.
Many organizations are also integrating Sigma-based rules that work across systems, or converting their legacy rules to Sigma for portability. Chronicle Detect includes a Sigma to YARA-L converter so that you can easily port or migrate existing rules from legacy systems to Chronicle.
Chronicle customers can also take advantage of Google Cloud Threat Intelligence for Chronicle, an applied threat intelligence service available to Chronicle customers. This service surfaces highly actionable threats in Chronicle environments based on Google’s collective insight and research into Internet-based threats. Using Threat Intel for Chronicle, security teams can take advantage of a curated, high fidelity threat intelligence service that allows you to focus on real threats in the environment and accelerate your response time.
Threat Intel for Chronicle is exclusively curated for enterprise customers by Uppercase, Google Cloud’s intelligence research and applications team. Select intelligence on attack patterns is gathered across Google’s vast array of networks and services, coupled with operational research for deconfliction, context and enrichment, and then applied to customer telemetry. The service provides Google Cloud’s perspective on threats across the internet, the analytic insights we glean, and surfaces them as relevant alerts for customers.
To help customers with incident response, Chronicle also now offers SOC playbook and orchestration- ready APIs and integrations with leading vendors such as Palo Alto Cortex XSOAR, D3 SOAR, SIEMplify, and Splunk Phantom. Chronicle instances, APIs and search parameters are accessible directly within SOAR platforms which enables customers to combine real-time threat detection and investigation with their SOAR playbooks.
We’re also excited to let you know about new global availability and data localization options. Chronicle now has expanded data center support for all capabilities, including Chronicle Detect, in Europe and the Asia Pacific region.
To read more about the Chronicle Detect announcement, check out Google Cloud blog. For more information, download the datasheet or contact our sales team.
